Introduction to JSON Web Token (JWT)
JWT or JSON web token is the most popular method to identify an authenticated user. The process of authentication typically consists of the user providing a username and password to the application, which then sends a request to the server with that information. The server then checks the provided information against a database of users and, if the information is correct, sends a JWT to the user. This token is then included in the header of subsequent requests to protected routes, allowing the server to authenticate the user without the need for them to provide a username and password with every request.
Why JWT is needed?
You might be puzzled why can't we send a normal JSON object and why we need to send it as a token. The reason behind using JWT is that, if the authentication server provides it as plain JSON, the client application's APIs will have no method of verifying that the material they are getting is correct. Because of this security concern, the auth server must communicate this data in a manner that the client application can verify. This is where the idea of a "token" comes in.
How JWT works?
A JWT is composed of three parts: a header, a payload, and a signature. The header and payload are Base64Url encoded JSON strings, and the signature is a hash of the header and payload concatenated with a secret.
Therefore the JSON web token looks like this:-
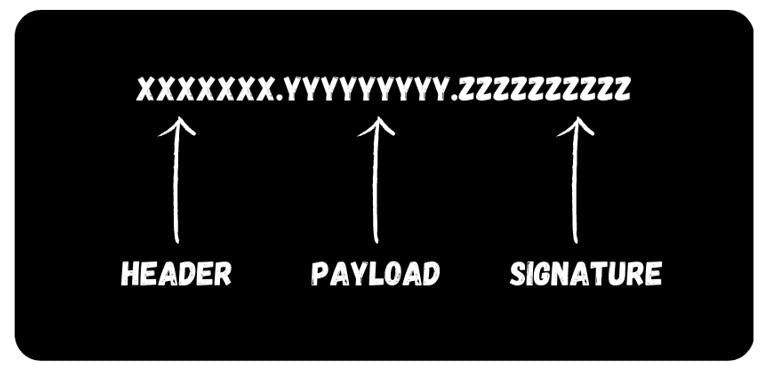
- Header
The header typically consists of two parts: the type of the token, which is JWT, and the signing algorithm being used, such as HMAC SHA256.
For eg:
{
"alg": "HS256",
"typ": "JWT"
}
This JSON is then Base64Url encoded to create the first component of the JWT.
- Payload
The payload contains the claims or the JSON objects. Claims are statements about an entity (typically, the user) and additional metadata. There are three types of claims: registered, public, and private claims.
Registered Claims: These are a set of predetermined claims that are not mandatory but are suggested to give a set of practical, interoperable claims. Some of them include: iss (issuer), exp (expiration time), sub (topic), aud (audience), and others.
Public Claims: These can be defined at will by those using JWTs. But to avoid collisions they should be defined in the IANA JSON Web Token Registry or be defined as a URI that contains a collision-resistant namespace.
Private Claims: These are the custom claims created to share information between parties that agree on using them and are neither registered nor public claims.
For eg:
{
"sub": "1234567890",
"name": "John Doe",
"admin": true
}
The payload is then Base64Url encoded to generate the JSON Web Token's second component.
- Signature
The signature is used to verify that the sender of the JWT is who it says it is and to ensure that the message wasn't changed along the way. The encoded header, encoded payload, a secret, and the algorithm mentioned in the header must all be combined to generate the signature portion.
The signature structure looks like this:
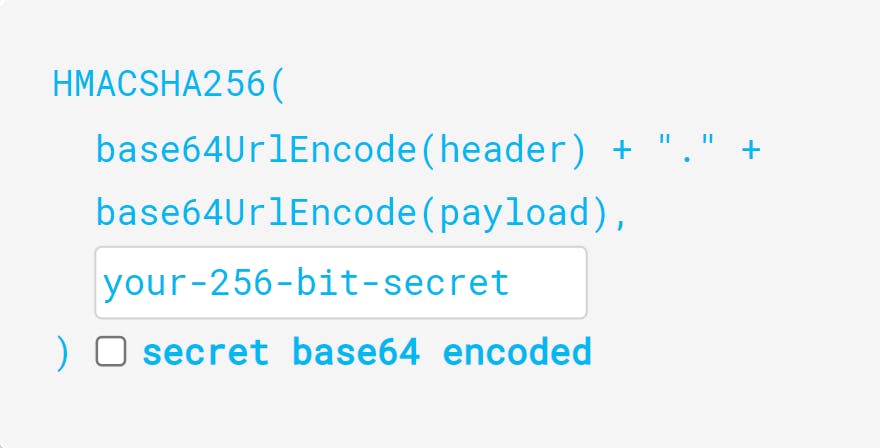
Structure of JWT
The result is three Base64-URL strings separated by dots that can be readily given in HTML and HTTP contexts.
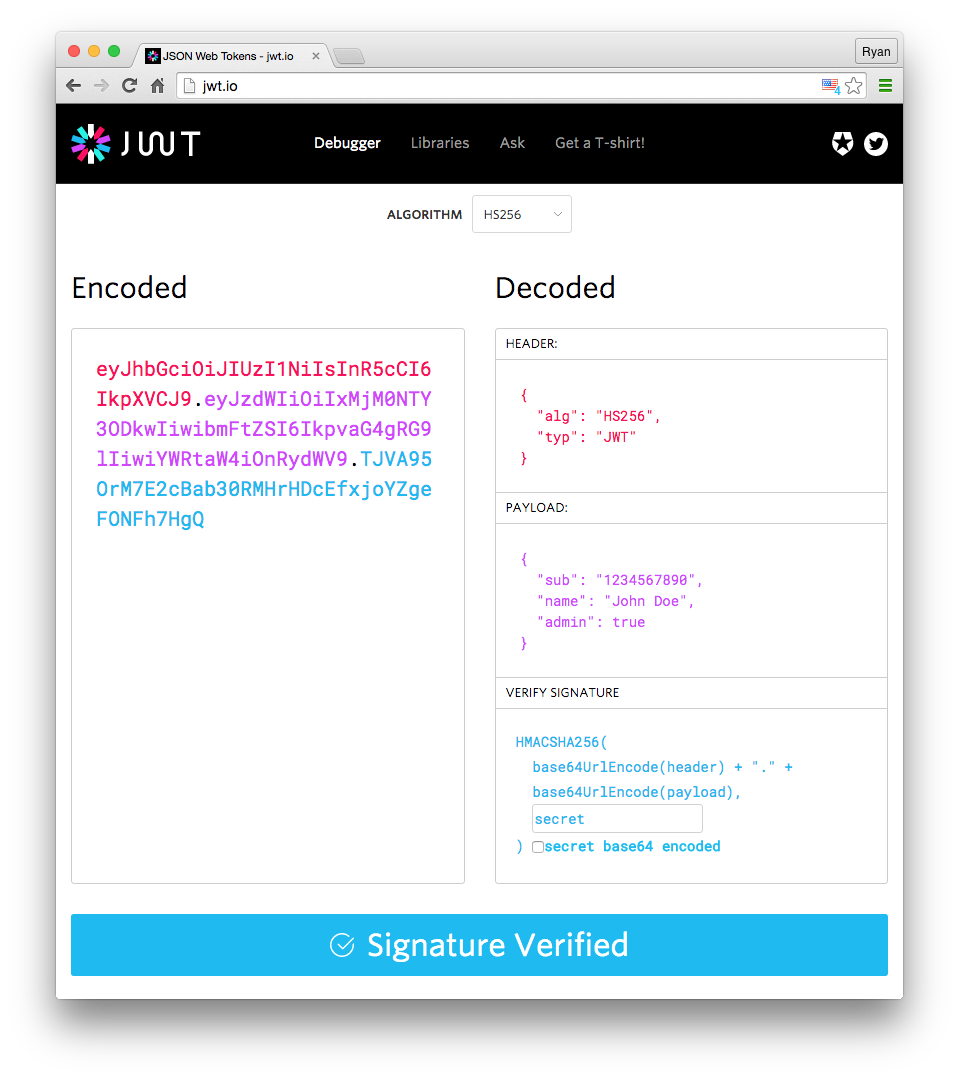
A JSON web token looks like this:
The red string is the encoded header, the purple is the encoded payload and the blue part is secret.

Conclusion
JWT is a powerful tool for authentication and authorization in web applications. It allows you to securely transmit information between parties and can be easily integrated into Node.js applications using the jsonwebtoken package. By using JWT, you can authenticate users without the need for them to provide a username and password with every request, and you can also securely transmit data between parties.
